As healthcare auditors know, healthcare organizations are mandated by the government to adhere to strict security and privacy measures with regard to protected health information (PHI), per the HIPAA guidelines. Audit trails and patient logs are needed to track who has access to a patient’s medical information, when that secure data was accessed, who accessed it, and if that access was appropriate. HIPAA also mandates that healthcare organizations regularly review and manage how their information is stored and accessed.

Selecting the Right Audit Trail Tools and Technologies:
- For example, you can create a purge job for the standard audit trail table and then the fine-grained audit trail table.
- In particular, it records the user logins, key system updates, changes to the files, and important transactions.
- Blockchain technology creates immutable audit trails, meaning once a record is entered, it cannot be altered or deleted — making it a game-changer for fraud prevention.
- By incorporating these elements, audit trails provide a robust framework for maintaining transparency and accountability across various systems and processes.
- There should be a timely and regular backup of this trial since electronic devices are always at risk of malfunctioning or being completely unusable.
- This level of transparency fosters trust among stakeholders and guarantees the reliability and credibility of data.
- This can reveal bottlenecks in workflows and processes that, once addressed, can streamline operations and reduce turnaround times.
Access to this information could assist in preventing future incidents of system failures, outages, corruption of data, hacking and detecting these issues in advance. If you had set CONTAINER to CONTAINER_ALL, then the purge job exists in the root, so you must run the DBMS_AUDIT_MGMT.SET_PURGE_JOB_STATUS procedure from the root. If you had set CONTAINER to CONTAINER_CURRENT, then you must run the DBMS_AUDIT_MGMT.DROP_PURGE_JOB_INTERVAL procedure from the PDB in which it was created. If you had set CONTAINER to CONTAINER_CURRENT, then you must run the DBMS_AUDIT_MGMT.SET_PURGE_JOB_INTERVAL procedure from the PDB in which it was created. If you had set CONTAINER to CONTAINER_ALL (to create the purge job in the root), then you must run the DBMS_AUDIT_MGMT.SET_PURGE_JOB_STATUS procedure from the root.

How Do You Maintain an Audit Trail?
Additionally, these documents allow for complete accountability of the individual and the whole board by providing a trace of any wrongdoings. It covers the protection of personal data and financial records, intellectual property and various other financial records. Intrusion detection is detecting attempts to break into an area and gain access. An IRS audit is a popular sort of external audit (and one that you don’t want!).
- Audit trails are a critical component of any transactional system, serving as the backbone for ensuring integrity, accountability, and traceability within various operations.
- Further, it is important to protect audit trail data, since the data should be available for use when you need it and it’s not useful if it contains errors.
- Regulatory frameworks increasingly require organizations to maintain detailed records of data access and processing activities.
- It also supports regulatory compliance by providing evidence during audits or investigations.
- If you decide to go the paperless route, you can avoid finding a place to store your paper accounting records.
Register now for your free, tailored, daily legal newsfeed service.
You audit trail must record the timestamp of the audit records before you can archive them. You can purge the entire audit trail, or only a portion of the audit trail that was created before a timestamp. You can create an archive of the unified and traditional database audit trail by using Oracle Audit Vault and Database Firewall.
Challenges Associated with Maintaining/Managing an Audit Trail
They document the lifecycle of a file or process, capturing every change, update, and approval. While the term might sound technical or even bureaucratic, audit trails are far from just a check-box for compliance. They’re the behind-the-scenes backbone of quality document control- bringing clarity, fostering accountability, and building trust across an organisation. In this article, we’ll explore what audit trails really are, why they matter beyond the regulatory lens, and some lesser-known but impactful ways they can elevate quality management systems. Intrusion detection is the process of identifying attempts to penetrate a system and gain unauthorized access. If audit trails have been set up to record appropriate information, they can be analyzed to help someone detect intrusions after the fact.
Countless teams and departments have transformed the way they work in accounting, HR, legal and more with Hyland solutions. Harness the power of a unified content, process and application intelligence platform to unlock the value of enterprise content. The views expressed on this blog are those of the author and do cash flow not necessarily reflect the views of New Relic.
- In this way, you can reduce the time spent reconstructing events, writing reports, and interviewing employees on events that are within the “business as usual” sphere.
- In this article, we’ll explore what audit trails really are, why they matter beyond the regulatory lens, and some lesser-known but impactful ways they can elevate quality management systems.
- In the worlds of business, finance, and IT, the term “audit trail” frequently pops up in conversations about accountability, transparency, and data integrity.
- You’ll often see them used day-to-day in financial, accounting, IT, security, and healthcare industries.
- Audit trails are like a digital security camera that records everything that is happening in a system, application, and network.
Organisations often implement logging mechanisms that store data in secure environments with restricted access. Plus, modern advancements such as blockchain technology and AI-driven audit analytics enhance how businesses track and analyse audit trails, making them more robust and resistant to manipulation. This guide dives deep into the definition of the audit trail, its importance across industries, and the best practices for implementation. By the end, you’ll also understand why businesses, governments, and healthcare institutions rely on audit tracking to deter fraud, keep laws in mind, and enhance operational efficiency. Consider the scenario of a system administrator updating client access permissions in a company’s database. Apply hash chains or per-record digital signatures to create cryptographic audit logs.
- The primary function of audit trails is to maintain the integrity of your documents, a crucial aspect today where data drives all the decisions.
- Audit trails are commonly used in financial systems, cybersecurity, healthcare, and legal surveillance to ensure accountability, detect anomalies, and facilitate investigations.
- When security breaches, financial discrepancies, or system failures occur, audit trails serve as a critical resource for forensic investigations.
- Use our one-click reporting feature to generate audits on time, tasks, workload and much more.
- They uncover operational inefficiencies, giving businesses the insights needed for smarter decisions.
- Use a centralized pipeline to validate, mask PII, add correlation IDs, and auto-generate evidence reports.
- Building an effective audit trail in a financial institution is critical for ensuring transparency, accountability, and adherence to regulatory standards.
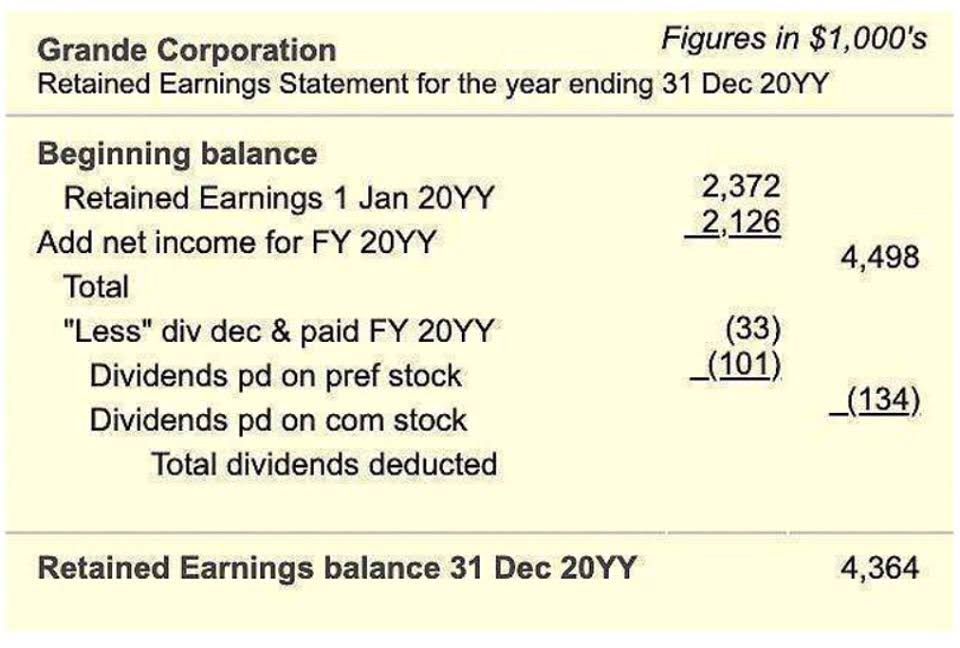
Meanwhile, regulatory bodies rely on audit trails to enforce compliance with financial regulations. Nearly all organizations use some version of audit logs to meet compliance, enhance visibility into user activities, and support data integrity. Audit trails serve as an essential component in the monitoring and verification of transactions within various systems. Retained Earnings on Balance Sheet They provide a chronological record of events and changes, offering transparency and accountability that is crucial for both compliance and operational integrity. From financial transactions to changes in critical system configurations, audit trails are indispensable in detecting anomalies, preventing fraud, and facilitating the reconstruction of events. Real-time monitoring of audit trails helps detect and respond to unusual behavior or potential security threats as they occur.